How To Read A Vulnerability Scan Report
How To Read A Vulnerability Scan Report - Web vulnerability scanning, also commonly known as ‘vuln scan,' is an automated process of proactively identifying network, application, and security vulnerabilities. This step includes the identification of assets and definition of risks and significant value for the devices to be used, such as a vulnerability scanner. Web the product security incident response team (psirt) drives adobe's vulnerability disclosure program. For example, some vulnerability scans are able to identify over 50,000 unique external and/or internal. Executive summary assessment overview results and mitigation recommendations each of these sections. Web a full vulnerability assessment report typically consists of the following elements: Best products cybersecurity companies vulnerability management edr. Web vulnerability scanning is a simple concept, but it’s a security measure that can make a world of difference. Web to get a better understanding of the vulnerability assessment process, let’s take a look at the following four stages: Web how to read a nessus report.
Web vulnerability scanning, also commonly known as ‘vuln scan,' is an automated process of proactively identifying network, application, and security vulnerabilities. Web the product security incident response team (psirt) drives adobe's vulnerability disclosure program. Csv (used in spreadsheets, databases) the html and pdf formats appear very. Web get started what is a vulnerability scanning report? How to leverage nessus scan reports for better vulnerability. Web a full vulnerability assessment report typically consists of the following elements: Web apart from that, being cautious with what rar files you open and using an antivirus tool that can scan archives would be a good security measure. Web to get a better understanding of the vulnerability assessment process, let’s take a look at the following four stages: Web learn more — the linkedin team last updated on aug 17, 2023 a vulnerability scan is a process of identifying and assessing the potential weaknesses and risks in your network, systems, and. Web vulnerability scanning is a process that identifies vulnerabilities in a computer system or network.
A nessus vulnerability scan report can be delivered in these formats: Best products cybersecurity companies vulnerability management edr. Learn more about it here. Program owners and clients don’t want to spend much time reading. Web the product security incident response team (psirt) drives adobe's vulnerability disclosure program. Csv (used in spreadsheets, databases) the html and pdf formats appear very. Web turning your nessus scan results into actionable reports helps you dynamically visualize the vulnerability assessment process. Web to get a better understanding of the vulnerability assessment process, let’s take a look at the following four stages: For example, some vulnerability scans are able to identify over 50,000 unique external and/or internal. Web how to read a nessus report.
Network Vulnerability Scanning and Why You Need it Now Concensus
A vulnerability scanning report is a document which records all findings after a vulnerability scan has taken its course. Web vulnerability scanning, also commonly known as ‘vuln scan,' is an automated process of proactively identifying network, application, and security vulnerabilities. Web in this video we discussed nessus vulnerability scan analysis, based on popular request by my subscribers. Web vulnerability scanning.
Online External Vulnerability Scan HostedScan Security
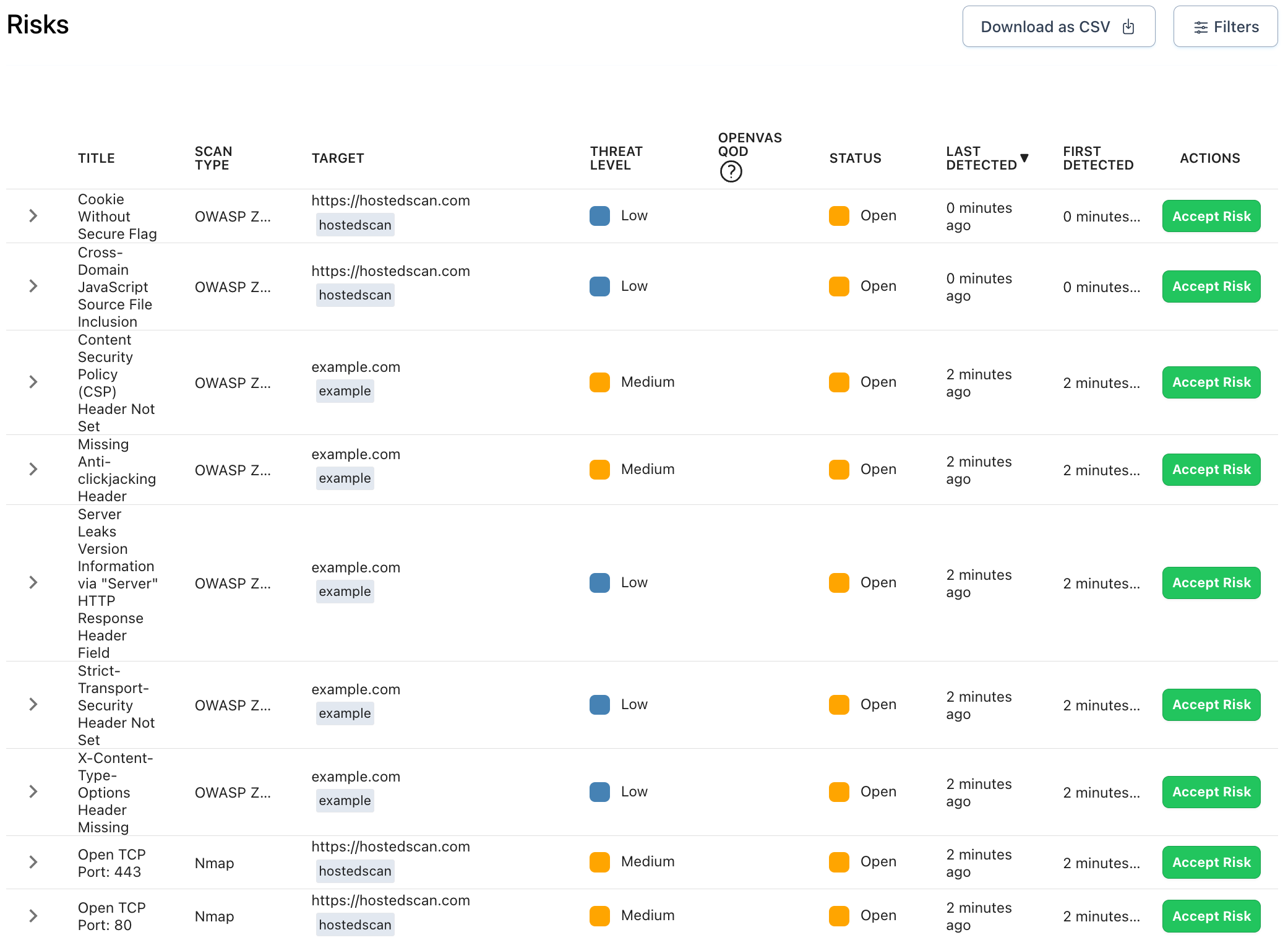
Web get started what is a vulnerability scanning report? Web an actionable vulnerability scan report identifies vulnerabilities that could pose a threat to your system, tells you the severity of each vulnerability, and provides remediation suggestions. Web vulnerability scanning is a simple concept, but it’s a security measure that can make a world of difference. Web a full vulnerability assessment.
What Is a Vulnerability Scan, and Why Is It Important?
Web how to read a nessus report. How to leverage nessus scan reports for better vulnerability. Web a full vulnerability assessment report typically consists of the following elements: Web a vulnerability description must be short, clear, and direct. Web vulnerability scanning is a process that identifies vulnerabilities in a computer system or network.
Web Vulnerability Assessment Report Template Template Resume
Learn more about it here. Csv (used in spreadsheets, databases) the html and pdf formats appear very. Web apart from that, being cautious with what rar files you open and using an antivirus tool that can scan archives would be a good security measure. For example, some vulnerability scans are able to identify over 50,000 unique external and/or internal. The.
Read Vulnerability Assessments Online
A vulnerability scanning report is a document which records all findings after a vulnerability scan has taken its course. For example, some vulnerability scans are able to identify over 50,000 unique external and/or internal. Web a full vulnerability assessment report typically consists of the following elements: I demonstrated the scan analysis using excel spreadsheet. How to leverage nessus scan reports.
What You Need to Know About Vulnerability Assessments SecureOps
Web get started what is a vulnerability scanning report? A nessus vulnerability scan report can be delivered in these formats: Web how to read a nessus report. Web vulnerability scanning is a process that identifies vulnerabilities in a computer system or network. Web a scan report includes current vulnerability information about hosts in your account (hosts you select at run.
Read Vulnerability Scan Complete SelfAssessment Guide Online by
The open vulnerability assessment system (openvas) started. I demonstrated the scan analysis using excel spreadsheet. Web vulnerability scanning, also commonly known as ‘vuln scan,' is an automated process of proactively identifying network, application, and security vulnerabilities. How to leverage nessus scan reports for better vulnerability. Web apart from that, being cautious with what rar files you open and using an.
Vulnerability Management Qualys
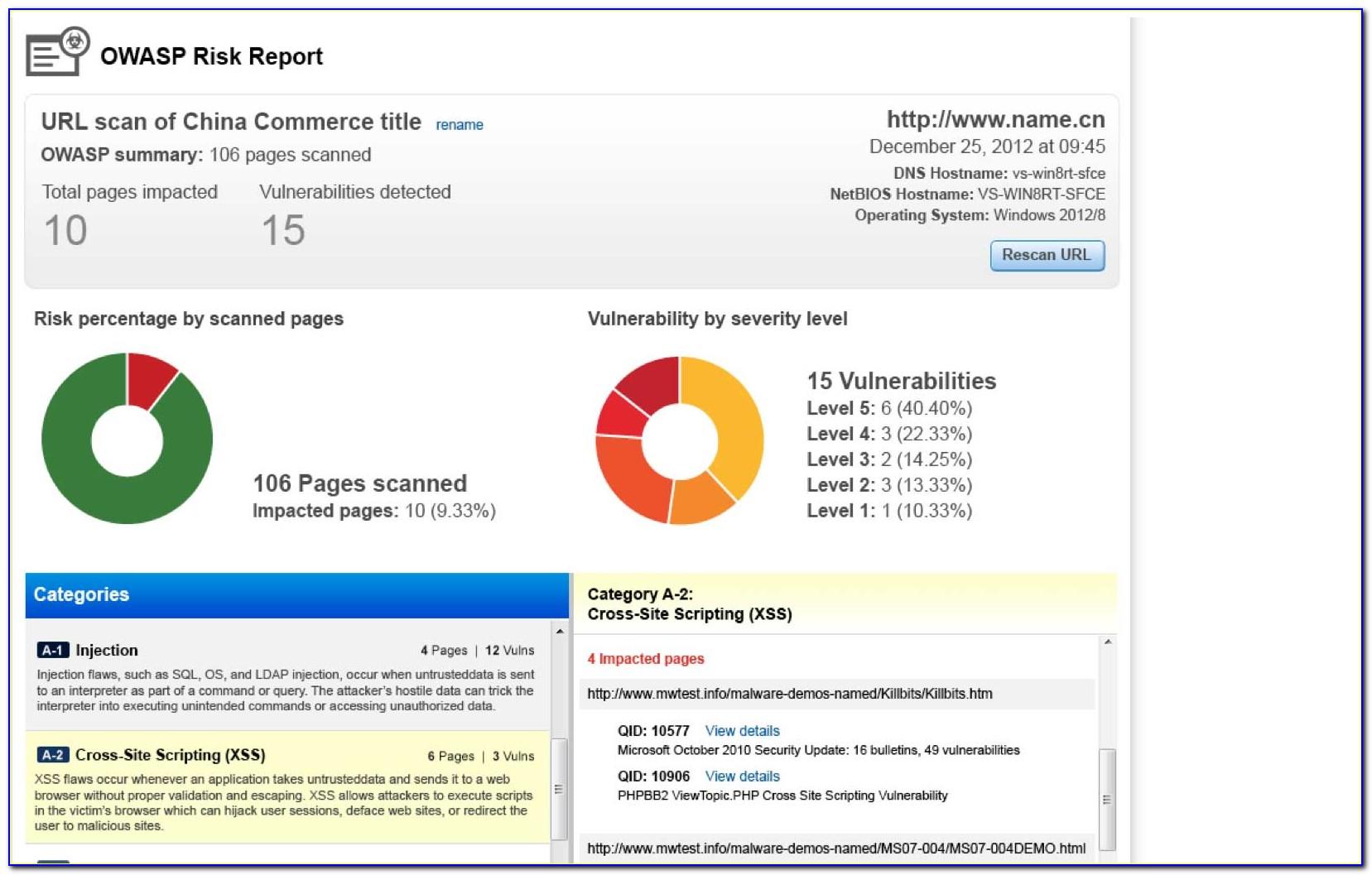
The amount of detail included in the report is based on your report template settings. I demonstrated the scan analysis using excel spreadsheet. Web the product security incident response team (psirt) drives adobe's vulnerability disclosure program. Web a full vulnerability assessment report typically consists of the following elements: A great way to describe a vulnerability in a short, clear way.
Labor Relations
Web in this video we discussed nessus vulnerability scan analysis, based on popular request by my subscribers. Web learn more — the linkedin team last updated on aug 17, 2023 a vulnerability scan is a process of identifying and assessing the potential weaknesses and risks in your network, systems, and. The severity of vulnerabilities is typically based on the common.
Austins Blog for CIST1001
Best products cybersecurity companies vulnerability management edr. Why should i run a scan report? It involves regularly scanning a network to check for vulnerabilities and weaknesses. A vulnerability scanning report is a document which records all findings after a vulnerability scan has taken its course. Learn more about it here.
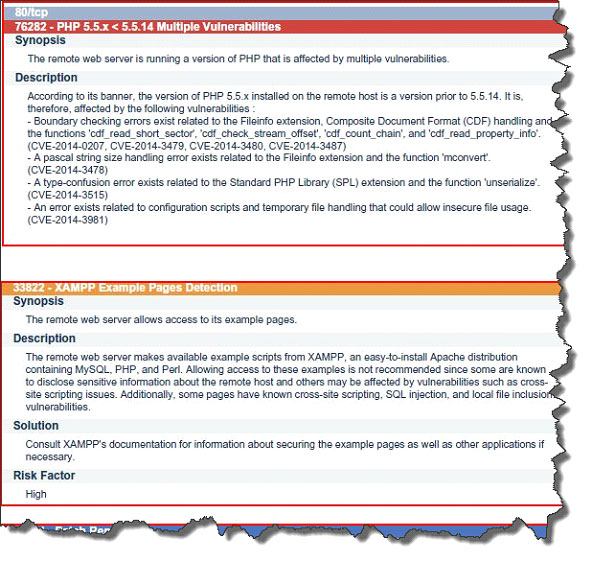
The Severity Of Vulnerabilities Is Typically Based On The Common Vulnerability Scoring System (Cvss) Provided By The Nist National Vulnerability.
A nessus vulnerability scan report can be delivered in these formats: Why should i run a scan report? For example, some vulnerability scans are able to identify over 50,000 unique external and/or internal. Best products cybersecurity companies vulnerability management edr.
I Demonstrated The Scan Analysis Using Excel Spreadsheet.
Web apart from that, being cautious with what rar files you open and using an antivirus tool that can scan archives would be a good security measure. Csv (used in spreadsheets, databases) the html and pdf formats appear very. A vulnerability scanning report is a document which records all findings after a vulnerability scan has taken its course. Web turning your nessus scan results into actionable reports helps you dynamically visualize the vulnerability assessment process.
Web How To Read A Nessus Report.
Web vulnerability scanning includes automated network and system scans. The amount of detail included in the report is based on your report template settings. Web vulnerability scanning, also commonly known as ‘vuln scan,' is an automated process of proactively identifying network, application, and security vulnerabilities. Executive summary assessment overview results and mitigation recommendations each of these sections.
The Open Vulnerability Assessment System (Openvas) Started.
Web an actionable vulnerability scan report identifies vulnerabilities that could pose a threat to your system, tells you the severity of each vulnerability, and provides remediation suggestions. Web vulnerability scanning is a simple concept, but it’s a security measure that can make a world of difference. It involves regularly scanning a network to check for vulnerabilities and weaknesses. Web a vulnerability description must be short, clear, and direct.